We're excited to announce the launch of our most comprehensive Node.js security training collection yet, covering all 25 of the most critical Common Weakness Enumerations (CWEs) that every Node.js developer needs to know about.
What’s new
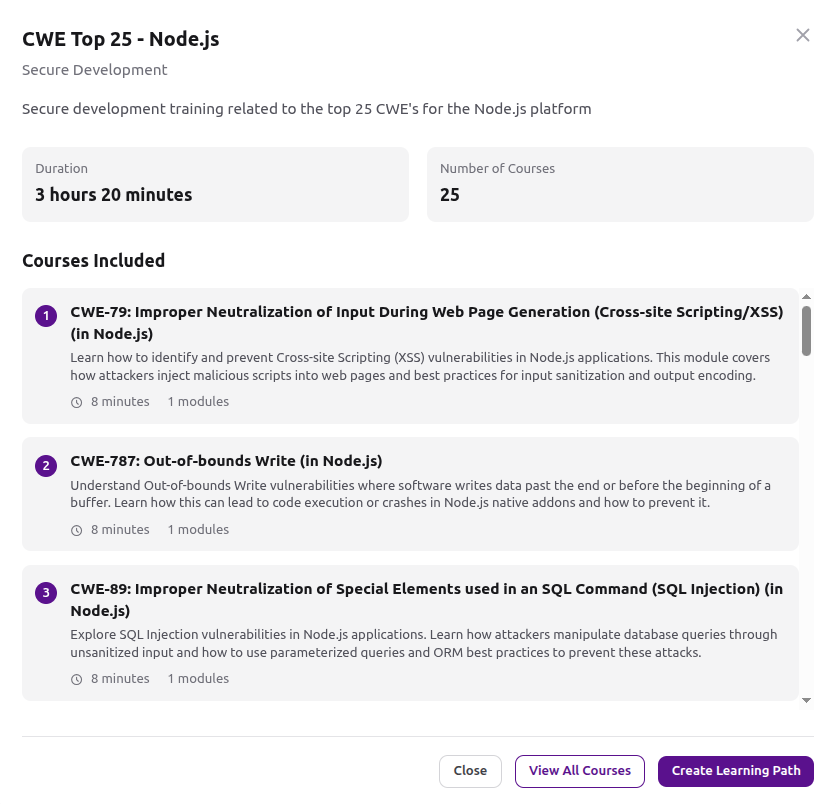
CWE Top 25 - Node.js
We've released 25 targeted security courses covering the complete CWE Top 25 list, specifically tailored for Node.js development. With 3 hours and 20 minutes of focused technical content, this learning path gives your development team practical, hands-on knowledge to identify and prevent the most dangerous software weaknesses.
Each 8-minute course is designed to fit into a developer's workflow without disruption, covering:
Injection vulnerabilities: XSS (CWE-79), SQL Injection (CWE-89), Command Injection (CWE-77, CWE-78), and Code Injection (CWE-94)
Memory safety issues: Out-of-bounds Read/Write (CWE-125, CWE-787), Use After Free (CWE-416), Buffer Overflow (CWE-119)
Access control weaknesses: Missing Authorization (CWE-862), Incorrect Authorization (CWE-863), Improper Authentication (CWE-287), Improper Privilege Management (CWE-269)
Data protection risks: Exposure of Sensitive Information (CWE-200), Deserialization of Untrusted Data (CWE-502), Hard-coded Credentials (CWE-798)
Request forgery attacks: CSRF (CWE-352), SSRF (CWE-918)
File security: Path Traversal (CWE-22), Unrestricted File Upload (CWE-434)
Resource management: Uncontrolled Resource Consumption (CWE-400), Integer Overflow (CWE-190)
Core security practices: Improper Input Validation (CWE-20), NULL Pointer Dereference (CWE-476), Missing Authentication for Critical Functions (CWE-306)
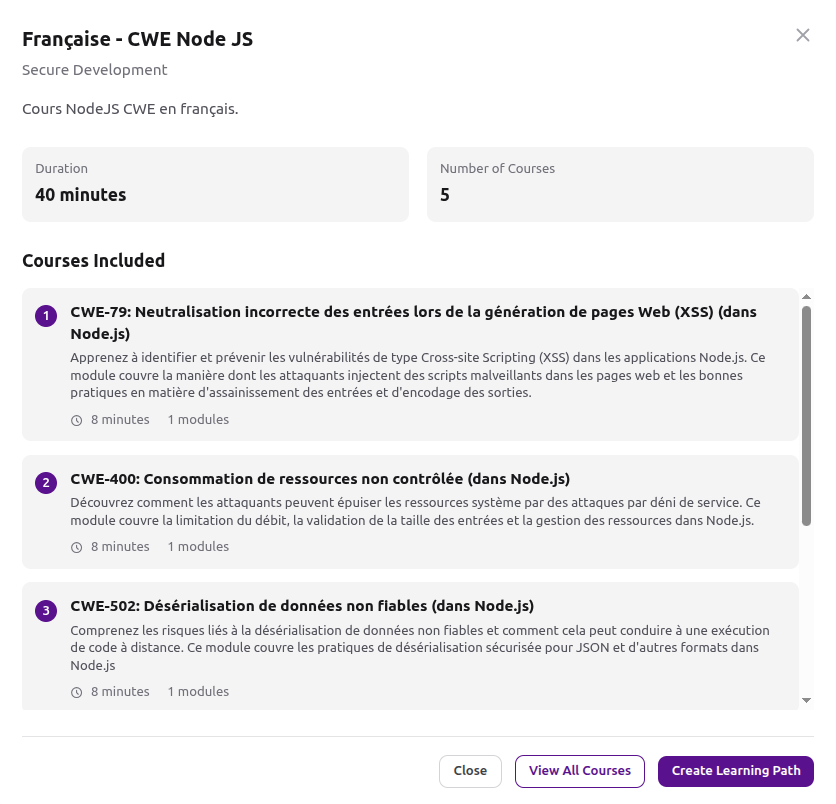
Française - CWE Node JS (New!)
For the first time, we're introducing French language security training for Node.js developers. The initial release includes 40 minutes of content covering 5 critical CWEs:
CWE-79: Neutralisation incorrecte des entrées lors de la génération de pages Web (XSS)
CWE-22: Limitation incorrecte d'un nom de chemin à un répertoire restreint (Path Traversal)
CWE-190: Dépassement d'entier ou rebouclage
CWE-400: Consommation de ressources non contrôlée
CWE-502: Désérialisation de données non fiables
More French courses are in development to complete the full CWE Top 25 coverage.
Why This Matters
These courses are built specifically for developers who need to ship secure code but don't have time for lengthy training programs. Here's what makes them effective:
Developer-Centric Approach
Written by developers, for developers
Focused on practical application, not theory
No security expertise required to get started
Short & Focused
8-minute modules that respect your team's time
Concise explanations that get straight to the point
Easy to complete during a coffee break or between tasks
Technical & Hands-On
Real Node.js code examples showing vulnerable patterns
Practical remediation techniques you can apply immediately
Covers both JavaScript and native add-on scenarios where applicable
Easy Deployment
Available as learning path templates, group leaders can create and assign these learning paths to their teams with just a few clicks. No need to manually curate courses or build curricula from scratch.
Who Should Take These Courses
Node.js developers who want to write more secure code
Development teams adopting secure coding practices
Engineering leaders building security into their SDLC
Anyone working with Node.js in production environments
Get Started Today
Ready to level up your team's Node.js security skills? Get in touch with us to get started.